As organisations increasingly rely on cloud providers like Microsoft, Amazon, and Google to store their data, I’ve noticed a common misconception:
“Our data is safe because it’s stored on a major cloud provider’s secure servers.”
Have you come across this statement before?
While the infrastructure used by major cloud providers has excellent security standards and their platforms offer robust features, believing this alone makes your data secure by default is a dangerous misunderstanding. Let’s explore why - and what else we need to do to ensure our data stays secure in the cloud.
We’ll discuss:
- The shared security responsibilities between you and your cloud provider
- Whether cloud services are truly secure by default
- Broader supply chain security concepts you should apply to your cloud strategy
Shared Security Responsibilities
Cloud providers typically operate on a shared responsibility model. This means that both the provider and their customers work together to secure cloud environments.
Depending on the type of cloud deployment model, customers may offload certain responsibilities to the provider—freeing up internal resources, which is a clear advantage. But that doesn’t mean you’re off the hook.
Here’s an example:
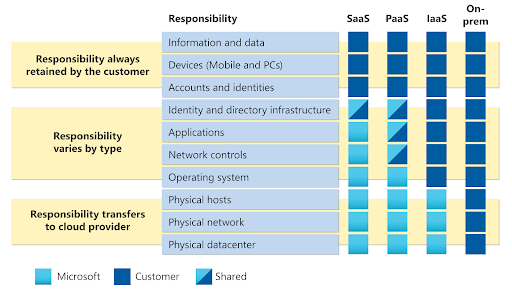
This is Microsoft’s cloud shared responsibility model.
As you can see, regardless of the cloud deployment used, Microsoft’s customers always retain responsibility over their data, endpoints, accounts, and access management.
For instance, if an attacker gains access to your data due to weak authentication practices or a malware infection on an unsecured laptop, Microsoft will not take responsibility for the breach.
That means the onus is on you to:
- Implement strong access controls
- Enforce acceptable use policies
- Maintain endpoint security
In other words, cloud infrastructure may be secure—but that doesn’t automatically secure your organisation’s data.
If your organisation has a mature cyber security posture, you’re likely already doing these things elsewhere. The cloud is not a silver bullet - it’s a tool. And like any tool, it must be used effectively to reap its benefits.
One challenge with cloud services is that security controls are not always intuitive to implement.
While major cloud providers aim to make their products more secure by default, many security features still require:
- A technical understanding to configure effectively
- Additional costs beyond standard licence fees
This creates two potential risks:
- Misconfigurations, which are a leading cause of cloud breaches
- False assumptions that certain features are active when they’re not
Let’s take Microsoft’s Data Loss Prevention (DLP) features as an example. DLP helps stop sensitive data from leaking. Although Microsoft promotes a “Secure by Design and Default” approach, full DLP functionality isn’t included in many basic licences.
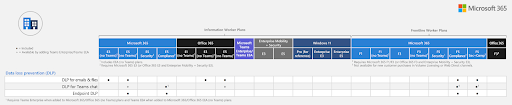
Depending on your setup, using a third-party security solution could be more cost-effective—but only if it integrates securely. Poor integrations can introduce vulnerabilities into your cloud environment.
Beyond the Cloud
Complacency isn’t just a cloud issue - it’s a supply chain issue.
When you store data in the cloud, your cloud provider becomes a critical supplier. Sharing data with suppliers means shared risk. If your provider is breached, your data may be exposed - even if the breach isn’t your fault.
Cloud providers rarely suffer breaches on their end, but:
- Outages, due to misconfigurations or attacks, can cause massive disruptions
- Remote access, often needed for support, can create vulnerabilities if poorly managed
- Multi-tenant access, common in cloud environments, can lead to data leakage if access controls aren’t tight
Before onboarding any provider, conduct due diligence:
- Ensure compliance with recognised cyber security standards like ISO/IEC 27001 or SOC 2
- Evaluate Service Level Agreements (SLAs) for uptime guarantees
- Review disaster recovery and incident response plans
- Verify secure access protocols and data separation policies
Microsoft Example
Microsoft makes it easy to assess their security posture via:
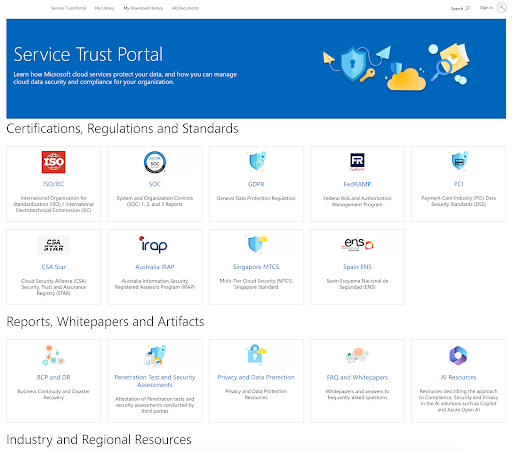
However, not all vendors are as transparent. You may need to:
- Request documentation
- Verify certifications
- Conduct independent assessments
Trust, but verify.
Cloud security is not set-and-forget. It requires ongoing reviews and real-time monitoring to ensure your suppliers stay compliant and your data stays protected.
Conclusion
Storing data in the cloud can enhance your security posture - but only if you remain vigilant and take an active role in managing the relationship with your provider.
Treat your cloud vendor as an active partner in your cyber security strategy. As your reliance on cloud services grows, your due diligence should scale accordingly.
Want to manage your cloud risk while embracing its benefits?
Get in touch—we can help you approach cloud security with confidence.
Photo by Growtika