
“Social engineering” is when threat actors use manipulation and deception to persuade a victim into doing either revealing something (such as credentials) or doing something (such as transferring money).
There’s not just one type of social engineering
There are many different types of attack that fall under the social engineering umbrella.
Most of us are probably familiar with or have experienced phishing, such as SMS phishing attacks. Like when you get a text from an unknown number that says “Hi it’s me! I lost my phone and I’m using this temporary one to contact you!”.
Other, less-well-known kinds of phishing include business email compromise (sometimes known as CEO fraud or invoice fraud), pharming and more targeted phishing called spear phishing. Like when a business gets an email saying “Hi, it’s [your supplier], we’ve recently changed our account details. Please update the account details you hold for us to ensure future invoices are paid correctly”.
But social engineering attacks aren’t limited to particular kinds of technology. They can be physical - for example, imagine you’re entering a restricted area and somebody is tailgating you, but you don’t check they have a valid authorisation pass because even though you don’t know them, you trust that they are there for legitimate reasons and want to be polite by holding the door open for them.
Despite the differences between the types, they all have something in common - the success of the attack depends on a response from a human.
Humans are vulnerable
People in the security industry constantly debate whether or not the biggest cyber risk is people. Whether it’s human error, accidental or inefficient actions, they all contribute to exposing risk – so threat actors target humans because they know they are susceptible.
Threat actors rely on the likelihood of vulnerable humans doing something wrong when they are targeted. They know that if someone is waiting for a file to be sent via email, the next email they get with a file attachment is more likely to be opened - and of course it might contain malware.
It’s all about psychology
It’s not solely about using technology or exploiting technical vulnerabilities.
Threat actors rely on things like:
- Urgency: it’s time-limited so you need to act promptly
- Authority: you’re more likely to comply with an authoritative figure (like your CEO!)
- Scarcity: you’ll miss out as there’s limited availability or supply of something
- Intimidation: you fear that something bad will happen if you don’t comply
- Consensus / social proof: what is being asked of you is expected or normal
- Familiarity / liking: you have an interest or are familiar with something
- Trust: you’re led to believe there’s a sense of safety or security
Awareness of social engineering
If you’ve seen an image of a fishing hook attached to an email during cyber security training, then it’s likely you’re aware of social engineering attacks like phishing.
Social engineering methods tend to follow trends, and are sometimes widespread campaigns. It’s important to keep up to date - keep an eye on the news for any common social engineering campaigns. For example, over the past year, there’s been a significant trend in a pharming campaign, where threat actors are impersonating popular brands in an attempt to capture victims’ personal and financial details.
Consider who’ll be impacted
People who are more likely to be targeted, such as board members and finance teams, should not only take part in the training but also have specific training on what to look out for. Contact details of executives and board members are often readily available on company websites, and attackers will use this to their advantage.
With business email compromise, threat actors are going to target those who are responsible for transferring money. So it’s necessary to understand not only the types of attacks, but who is most likely to be impacted by them.
Training for employees should take into account how they need to be wary of requests from board members that don’t align with their usual behaviour, like requesting iTunes vouchers.
The request might sound strange but if you believe who the request is coming from, you may still fall for it. Gift card scams are an easy way for threat actors to get money as they will often sell the gift cards online at a discounted rate.
Communication is key in many social engineering attacks. When you get a strange or unusual request, it’s always best to verify it using another communication method.
Test for assurance
As well as doing cyber security awareness training, it’s sensible to do phishing testing. Regular simulated phishing testing helps to provide assurance of the non-technical “human” controls. It’s a practical way of showing users the different methods that threat actors might use, and how they can check if an email is legitimate or not.
You could also set up some non-technical penetration testing, where the tester tries to find weaknesses in your physical security controls. That might be as simple as trying to tailgate a member of staff through the front door.
What to look for
Typically there’s lots of common things to look out for, including:
- Spoofed email addresses - using the Cydea domain as an example, the real sender may look like “Employee” <employee@cydea.com>, with the spoofed address being “Employee” <employee@cydéa.com>. At a quick glance the accent within the email address may be overlooked, so it’s worth paying greater attention to ensure if it’s legitimate or not
Grammar, punctuation and spelling mistakes
- Links - they’ll often be used to take you to a malicious site, this could be asking you to enter your account credentials to “verify” your account which is really when the threat actor steals your password
- Malicious attachments
- Being asked for personal, financial or sensitive information
- Being asked to change payee details or transfer funds
A phishing email can look like this:
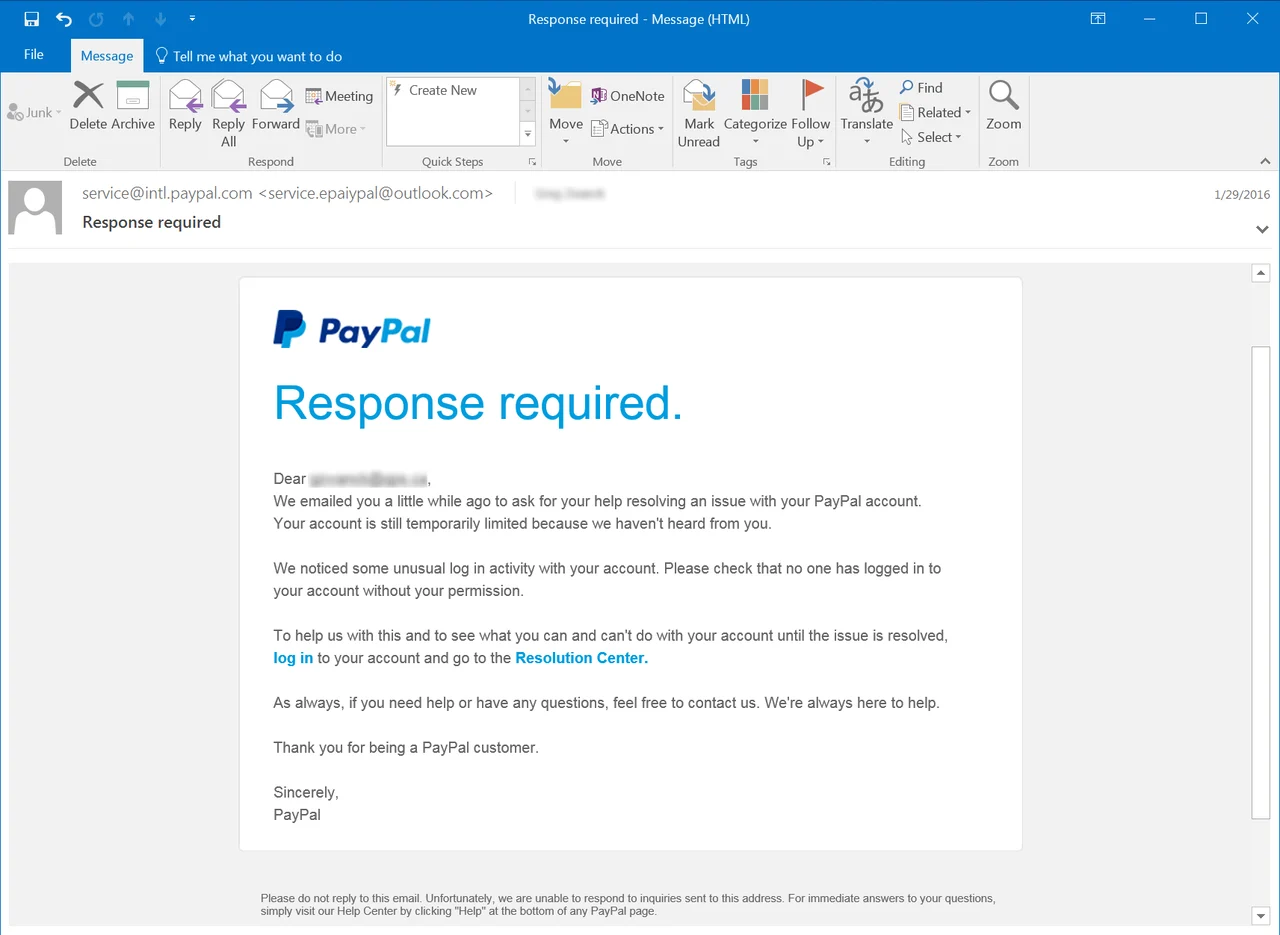
Image from: KnowBe4 https://www.knowbe4.com/phishing
Look closely and you can see the signs:
- the email address says “Paypal” but is actually an account at outlook.com
- links are suspicious because they ask you to log in and therefore would likely be passing your credentials to the attacker
- context is also very relevant here… the email suggests they’ve recently helped you with an issue with your account. But if you know you haven’t contacted them or had any issues then it shouldn’t be of concern. This however is sometimes how they catch people out as the context may be coincidentally relevant to you.
Hook, line and sinker
Social engineering attacks are common, particularly phishing as it’s very cheap and easy for a threat actor to send out lots of phishing attack emails.
Threat actors are very good at creating convincing campaigns, and their success relies on victims feeling pressured into doing something, or believing they are doing something to be helpful for someone they know.
It goes without saying, no one’s immune from a social engineering attack.
Headline photo by ThisisEngineering RAEng on Unsplash