
Most organisations already follow a commonly known control framework or may have a custom framework that is made up of controls from common frameworks.
These might include international frameworks like ISO 27002, CIS Critical Security Controls or NIST Cybersecurity Framework. Or, national frameworks like Cyber Essentials or SOX.
Your framework all depends on how it works for your organisation. It may be down to a third party expectation that requires you to certify to a framework, or you may be regulated and therefore require a certain framework. If you don’t have a control framework, we’ve previously given some guidance on how you can select one.
Broadly speaking, existing frameworks cover a variety of controls, but you may consider creating a custom framework in some cases. Whether that involves combining frameworks or creating new controls, is up to you.
So, why not align your control framework with your risk scenarios?
If you want to be able to manage risk effectively and understand what you’re doing, or what to do, to protect the risk you may be exposed to, then it’s key to know what controls you have or require.
First, you need to understand how you’ll treat risks, and that’s dependent on your risk tolerance. Regardless of whether your risk management strategy method is treat, transfer, tolerate or terminate, you still can align your risk scenario back to a control.
And not just one control. A risk scenario is not one-to-one but can be one-to-many controls. It all depends on what the risk is and what controls you have or are aware that you need to implement to manage the risk.
What does it look like?
The majority of controls treat risk, but there’s some that contribute to transferring the risk.
Let’s take a look at a risk scenario and consider what our risk management plan could look like:
Criminals (Source) + Ransomware (Event) = Business Disruption (Consequence)
- Using ISO 27002, we could manage risk by:
- Protection against malware (8.7)
- Management of technical vulnerabilities (8.8)
- Segregation of networks (8.22)
If you use a combination of control frameworks, you could also consider or may already have in place:
Test data recovery (CIS Controls: 11.5)
Continuous monitoring (NIST CSF: DE:CM)
Going beyond defined control frameworks is another option, as such managing risk by:
- Cyber insurance, to transfer risk.
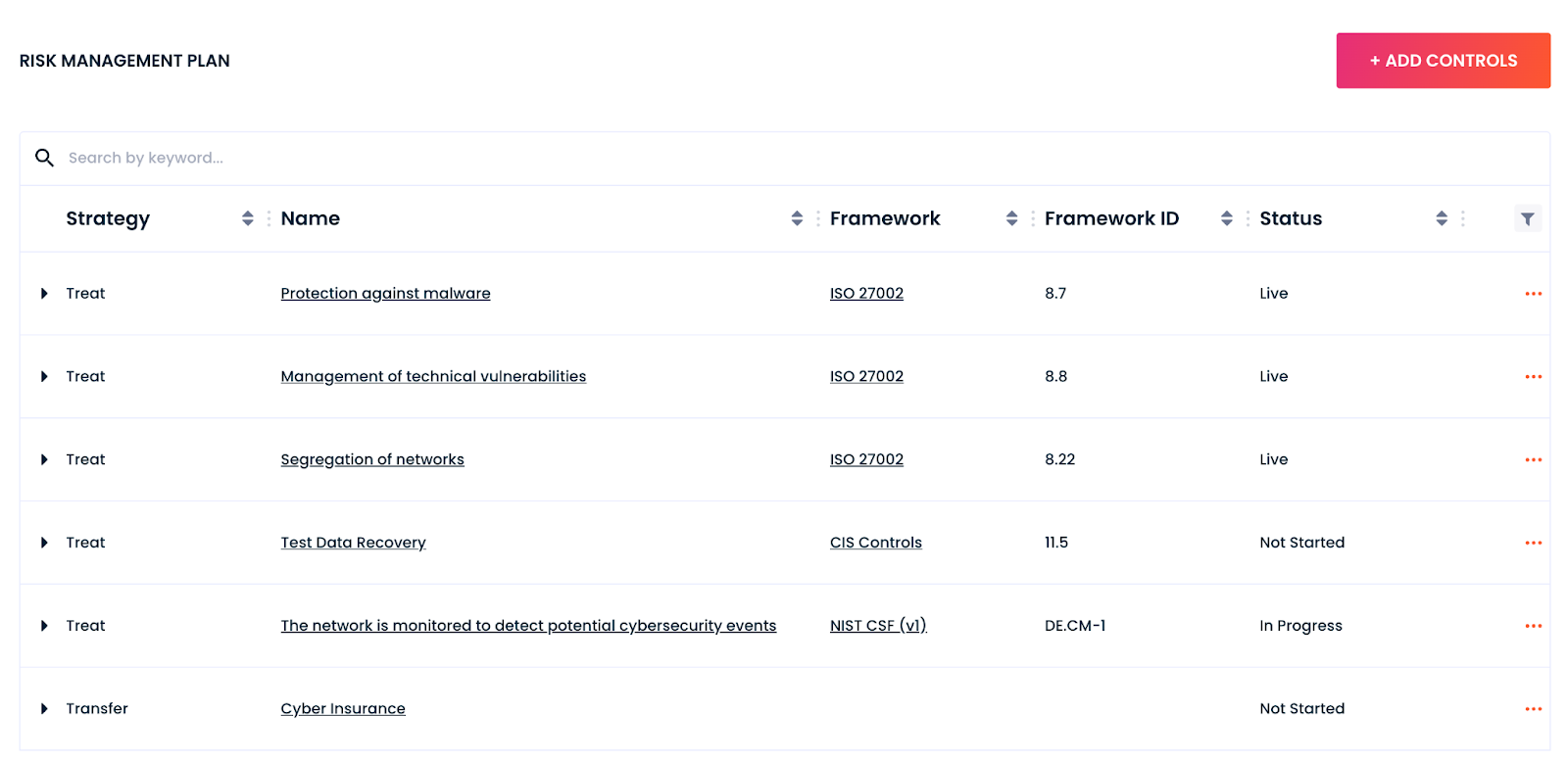
We use risk management plans in the Cydea Risk Platform to capture controls linked to risks. When linking controls to your risk scenarios, it doesn’t just have to be the current controls you have established. Think ahead to what other compensating controls may help to reduce your exposure to risk, and start to plan when you can achieve them. We capture this in the platform using implementation statuses, such as “live”, “in progress” and “not started”.
It’s equally important to assign owners to the controls aligned with your risk scenarios. With any risk management plan, ownership is crucial to delegate responsibility to ensure they’re being implemented and managed effectively.
Photo by Marcus Winkler on Pexels