
In my previous blog post, From Cop to Consultant, I shared how transferable skills helped me transition from being a police officer to a consultant. In this post, I’ll dive deeper into one specific skill set: police interview techniques. These methods have surprising and highly effective applications in consulting,particularly in the field of cyber security.
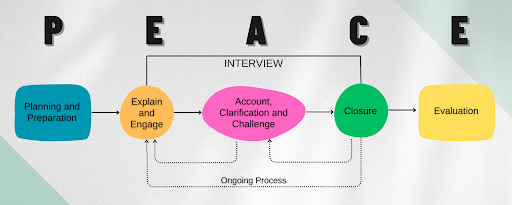
A key technique I’ll explore is the P.E.A.C.E model, a structured approach to interviewing that stands for:
- Preparation and Planning
- Engage and Explain
- Account, Clarification, Challenge
- Closure
- Evaluation
Originally developed for investigative interviews, this model is designed to encourage detailed, open responses and uncover crucial information through clarity and structure.
But the P.E.A.C.E model isn’t just for law enforcement, it’s a powerful framework that can be adapted to consulting engagements, such as conducting a cyber risk assessment with a Chief Information Security Officer (CISO). Its principles, including thorough preparation, building trust, and clarifying complex issues, can help consultants gain deeper insights and deliver actionable, effective solutions. Let’s explore how these police interviewing techniques can be applied to the world of consulting.
Preparation and planning: The foundation of success
As Benjamin Franklin said, “By failing to prepare, you are preparing to fail.” This couldn’t be more relevant for interviews, whether in policing or consulting. Despite what TV shows might suggest, police interviews don’t just happen on the fly, they require preparation, from reviewing evidence to setting clear agendas. The same principles apply to consulting, where preparation can make the difference between a productive meeting and a missed opportunity.
Before meeting a client, research their organisation, the roles of the individuals you’ll be speaking with, and their priorities. This understanding helps tailor your approach and build rapport. Just as a detective identifies their “points to prove,” you should define clear objectives for the meeting. For a cyber security risk assessment, for example, this might include identifying critical assets or evaluating existing security measures. Clear objectives keep the conversation focused and ensure you gather the insights you need.
I never went into a suspect interview without a plan, and the same applies when meeting a client. Your plan doesn’t need to be complicated but should outline key topics, potential questions, and supporting materials like previous reports. A solid plan ensures you don’t miss critical details and provides a fallback if the conversation stalls. Whoever you’re interviewing, preparation is the foundation of meaningful, productive discussions.
Engage and explain: Building trust
In both policing and consulting, rapport is essential. While building trust with someone in custody could be challenging, connecting with victims and witnesses required active listening and genuine empathy,skills that translate seamlessly to client engagements. Demonstrating that you value your client’s time and insights fosters a collaborative atmosphere, paving the way for a productive discussion.
Just as investigators explain their questioning, consultants must clarify the goals of their engagement. In a cyber security risk assessment, for example, make it clear that the aim is to strengthen security, not just highlight weaknesses. Setting clear expectations and explaining how their input shapes the process builds trust and encourages openness, setting the stage for a successful conversation.
Account, clarification, challenge: The Funnel Technique
Now that the preparation is complete and the rapport is established, the path is laid for interviewing.
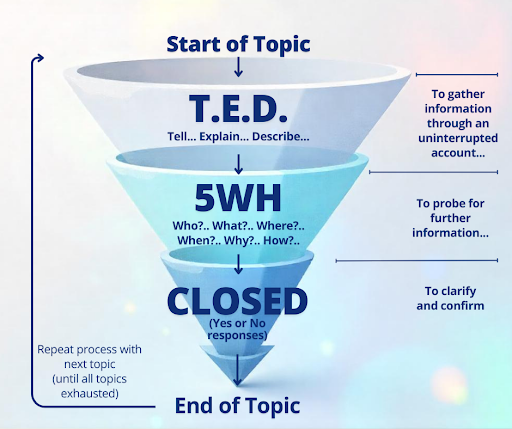
The following structured approach is the Funnel Technique and mirrors the methods taught to me as a detective for interviewing suspects and witnesses.
It starts with broad, open-ended questions to encourage detailed responses, then narrows down to specific areas using probing and closed questions for clarity. This systematic method ensures comprehensive coverage and builds a clear understanding of the client’s security posture.
You should look to follow this process for each key topic you identified whilst planning.
1. TED Questions
At the beginning of the funnel, open-ended TED questions,Tell, Explain, Describe,are particularly powerful. TED questions provide the person you are interviewing with more space to share their experiences in their own words and share more detailed information.
For example, instead of asking closed-ended questions like, “Do you have a process for managing third-party risks?” which can be answered with a simple “yes” or “no,” you could ask:
- Tell me about your process for managing third-party risks.
- Explain how you evaluate and mitigate potential risks associated with third-party vendors.
- Describe a time when you had to address a security incident involving a third-party vendor.
It’s important to avoid interrupting when the person is answering your TED question, as it can derail the flow of information or make the client less willing to share candidly. Their responses often provide deeper insights into their processes and can introduce new topics that you can explore further later in the conversation.
2. 5 WHs
Once TED questions have opened the door to detailed and expansive answers, the next step in the funnel involves using the 5WHs: What? Where? When? Why? How?
These questions help you dig deeper into the details uncovered earlier, ensuring a comprehensive understanding of the topic at hand. For example, in a cyber security context, you might follow up with questions like:
- What controls are in place to manage third-party risks?
- Where do you see the greatest vulnerabilities in your supply chain?
- When was your last third-party risk assessment?
- Why did you select your current vendor vetting process?
- How do you address incidents related to third-party breaches?
The 5WHs are invaluable for organising and clarifying information and are still open-ended to encourage more detailed answers. They guide the conversation in a structured way, allowing you to explore specific areas without making the discussion feel rigid.
3. Closed Questions
Once you have exhausted your open-ended questions, the final stage of the funnel technique involves using closed questions to confirm details and clarify any remaining uncertainties. Closed questions help solidify your understanding and ensure alignment with the client. Examples include:
- Do you have a dedicated incident response team?
- Have you conducted a vulnerability assessment in the past 12 months?
- Are you compliant with ISO 27001?
Finally, if you identify discrepancies, use respectful questioning to explore these areas further. Avoid sounding accusatory, focus on understanding and resolving gaps in information.
This step ensures that nothing important is missed and prepares you to deliver a well-rounded assessment report.
Closure: Wrapping Up
In policing, wrapping up an interview means ensuring all key points are covered, giving the interviewee a chance to clarify their statements, and explaining what will happen next. The same principles apply when working with clients.
The closure stage is where everything comes together, ensuring you and your client leave the conversation aligned. Summarising key points is crucial for clarity and alignment. Highlight the main insights to reassure the client you’ve been listening and provide an opportunity for them to clarify or expand on anything missed.
Before wrapping up, invite questions to address any lingering concerns and avoid misunderstandings. Finally, outline the next steps,whether it’s preparing a report, scheduling follow-ups, or setting a timeline. A clear, purposeful close leaves the client confident in the progress and next steps
Evaluation
Like a police officer reviewing all the evidence after an interview, your work isn’t done when the conversation ends. After gathering information from your meeting, take time to review and analyse it, identifying patterns, risks, or vulnerabilities in their cyber security strategy.
The findings gained from following this method will allow you to develop actionable, practical recommendations that help your client and their posture.
Finally, reflect on your performance. Consider what worked, where you could improve, and how to ask better questions or frame discussions differently. Continuous reflection sharpens your skills, enhances your practice, and builds trust and professionalism with clients.
Final Summary
Interviewing isn’t just for law enforcement, it’s a powerful skill for consultants, especially in cyber security.
The PEACE model stands out as a clear framework for success, guiding consultants from preparation to thoughtful evaluation. By starting broad and narrowing the focus with open-ended questions, consultants can gain a deeper understanding of client challenges and uncover hidden risks, enabling smarter recommendations and better outcomes.
What stands out most is the reminder that transferable skills, whether from law enforcement or another field, are invaluable in consulting. The ability to actively listen, empathise, and think critically are all traits that make a consultant more effective. By blending these skills with structured techniques, professionals can elevate their practice, deliver exceptional value, and build the trust essential to long-term success in consulting.
Photo by Christina @ wocintechchat.com on Unsplash